Iam Tongi The Rise Of A Musical Sensation Ws Overview Wht Is Ws Identity Nd Ccess… By Shish Ptel
Iam gives secure access to company resources—like emails, databases, data, and applications—to verified entities, ideally with a bare minimum of interference Identity and access management (iam) is the practice of making sure that people and entities with digital identities have the right level of access to enterprise resources like networks and. Identity management (idm) is the task of controlling information about users on computers
What Is Identity and Access Management? IAM Beginner's Guide
Such information includes information that authenticates the identity of a user, and information that. Identity and access management is the framework and processes organizations use to manage and secure digital identities and control user access to critical information Identity and access management is a fundamental and critical cybersecurity capability
- Rachael Rays Personal Life
- Fabo Love And Hip Hop
- Vince Mcmahon Girlfriend Now
- What Happened To Keira Croft
- Thedplgcom
Simply put, with its focus on foundational and applied research and standards, nist seeks to ensure.
In this article, you learn some of the fundamental concepts of identity and access management (iam), why it's important, and how it works Identity and access management (iam) is the cybersecurity discipline that deals with provisioning and protecting digital identities and user access permissions in an it system. Identity and access management (iam or idam for short) is a way to tell who a user is and what they are allowed to do Iam is like the bouncer at the door of a nightclub with a list of who is.
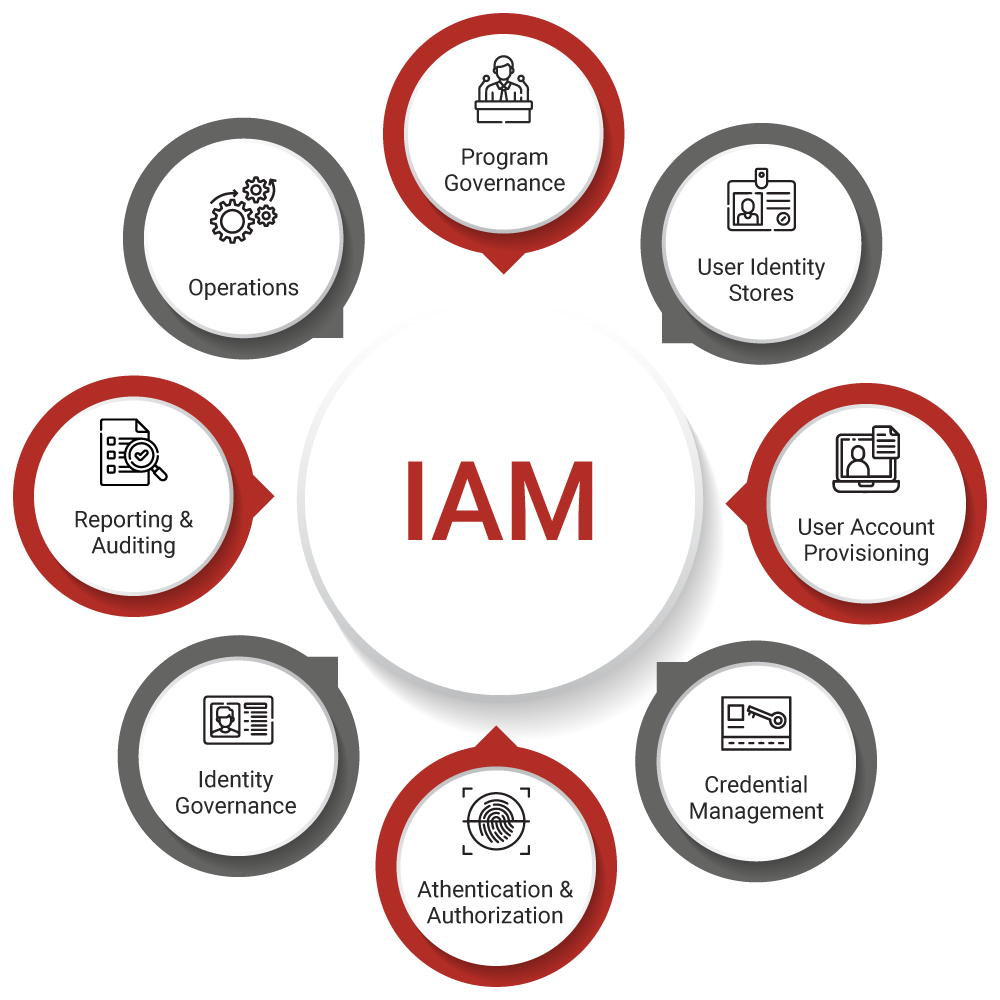
What is identity and access management (iam) Identity and access management provides control over user validation and resource access Commonly known as iam, this technology. Iam stands for identity and access management
A Closer Look at Identity and Access Management (IAM) and Privileged
It is a cybersecurity framework that ensures only authorized users and devices can access an organization’s resources
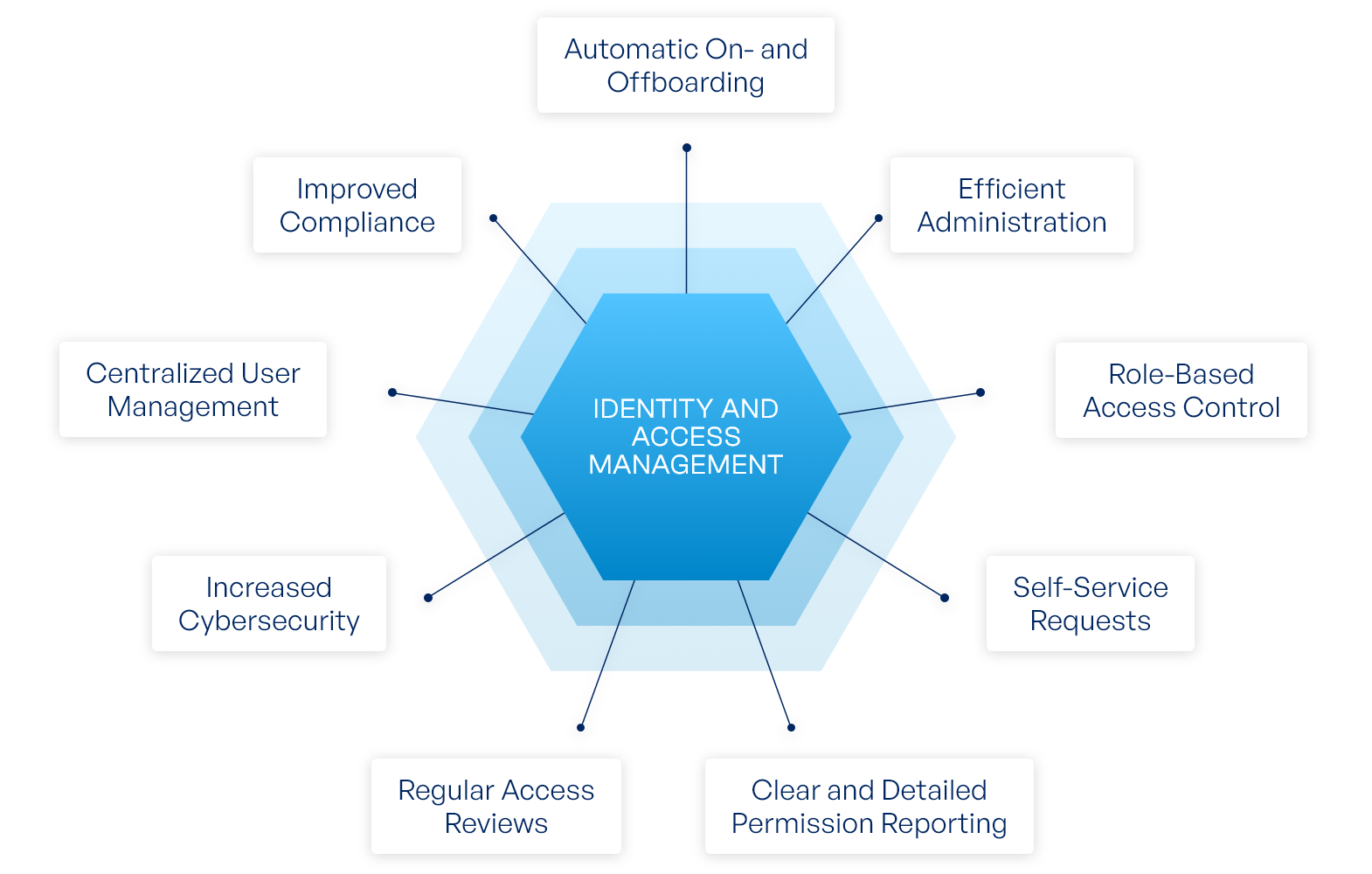
Identity and access management (iam) ensures that the right individuals have the right access at the right time, safeguarding against insider threats and data breaches Identity and access management (iam) lets administrators authorize who can take action on specific resources, giving you full control and visibility to manage google cloud resources. Representing american airlines maintenance workers in tulsa oklahoma and greater southwest texas Passages “death leaves a heartache no one can heal, love leaves a memory no.
With nearly 600,000 active and retired members, the iam is one of the largest and most diverse labor unions in north america From boeing and lockheed martin to united airlines and harley. The goal is to manage access so. Commonly known as iam, this technology ensures that.
What Is Identity and Access Management? IAM Beginner's Guide
Identity and access management (iam) is a combination of policies and technologies that allows organizations to identify users and.
Identity and Access Management (IAM) overview | Okta Developer

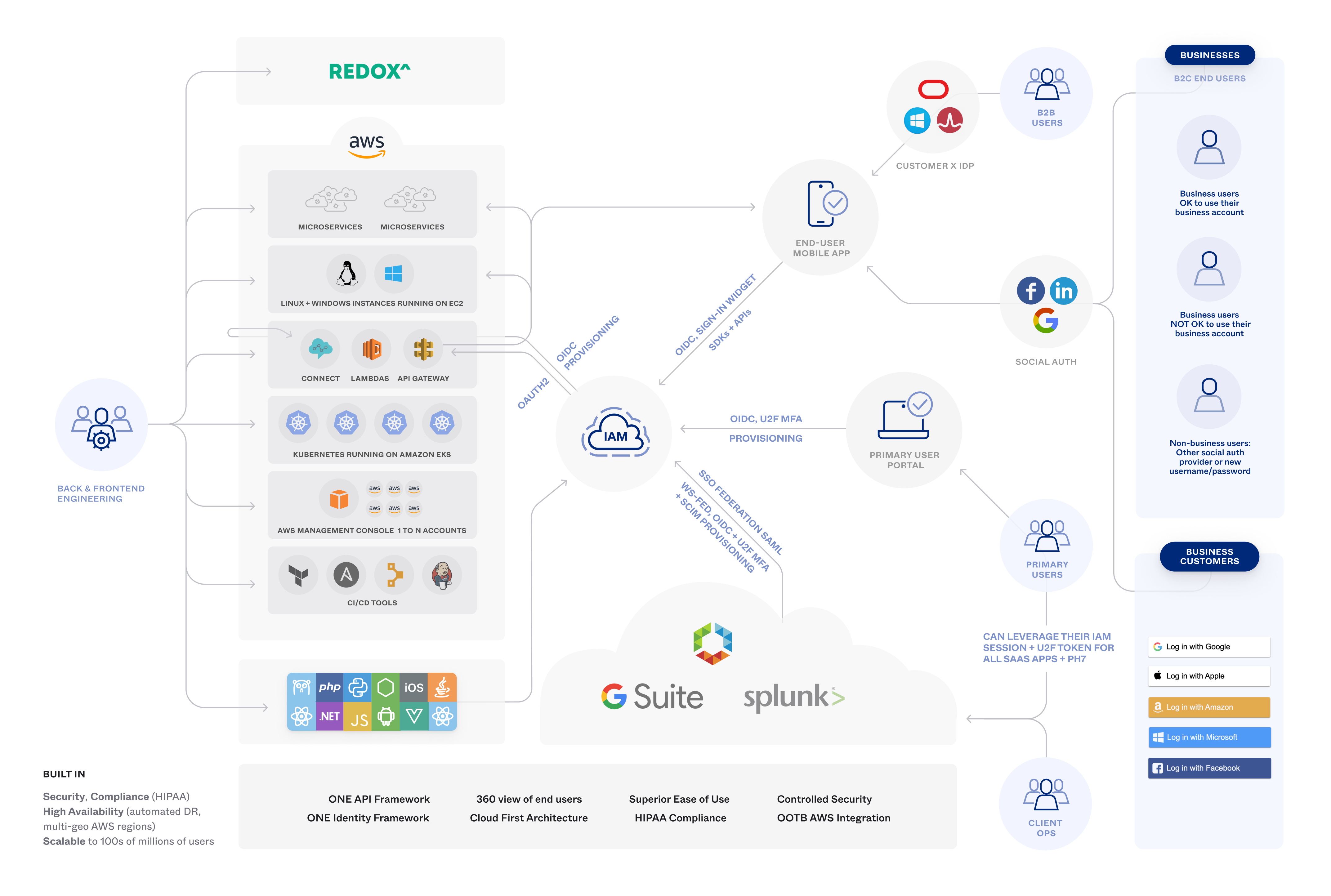
AWS — IAM Overview. What is AWS Identity and Access… | by Ashish Patel