Securely Connect RemoteIoT VPC AWS Not Working - A Guide
It can feel pretty frustrating when you have your remote internet-connected gadgets, those helpful IoT devices, and they just won't talk to your private cloud setup, your VPC, over in Amazon's web services. You've got everything lined up, or so you think, to get those bits of information flowing safely, but nothing seems to happen. It's like having a phone that won't dial out, even though you know the number is correct. This situation, where your remote IoT connection to an AWS VPC just isn't cooperating, is something many people run into. It’s a common snag, and it often comes down to a few key areas that need a closer look.
You’re trying to make sure that data from your faraway devices gets to where it needs to be without any unexpected detours or unwelcome guests. That means making sure the path is not only open but also protected. When it's not working, it can be a real head-scratcher, like trying to find a tiny piece of a puzzle that’s keeping the whole picture from coming together. We often think about the device itself, or maybe the cloud service, but the connection between them has many moving parts, so to speak, that need to line up perfectly.
This guide is here to help you sort through those tricky bits. We’ll go over some of the usual suspects that cause these connection hiccups, especially when you're aiming for a secure setup. By taking a closer look at the common reasons why your remote IoT might not be securely connecting to your AWS VPC, you can start to figure out what’s amiss and get things running smoothly. It’s about making sense of the puzzle pieces, really, and getting your devices to chat with your cloud environment in a way that keeps your information safe.
Table of Contents
- What is going on when your remoteIoT cannot connect to AWS VPC?
- Are the network settings holding things back for your securely connect remoteIoT?
- Is your device talking the right language for securely connect remoteIoT communication?
- What about identity and access for your remoteIoT in AWS VPC?
- Could your firewall be blocking securely connect remoteIoT traffic?
- How do you find out what is really happening with your remoteIoT VPC connection?
- What can make your remoteIoT connections to AWS VPC more dependable?
- Where do you go when you need more help with your remoteIoT VPC connection?
What is going on when your remoteIoT cannot connect to AWS VPC?
When your remote IoT device just won't make a proper connection to your private cloud space in AWS, it can feel like you're speaking different languages. This kind of problem is pretty common, and it usually means there's a disconnect somewhere in the chain that lets your device send its information to your cloud setup. Think of it like trying to send a letter, but the address is a bit off, or the post office isn't quite sure where to send it. The core idea is that your little device, perhaps out in the field, needs to send its data to a specific, protected spot within your AWS account. This spot is your Virtual Private Cloud, or VPC. It’s your own isolated section of the AWS cloud where you keep your important applications and data. For the connection to be successful, a lot of things have to line up. You need the right pathways open, the correct permissions set up, and the device itself has to be set up to talk to the right place in the right way. It's often a case of checking each step along the way, from the device's own settings to the rules you've put in place within your AWS account. Sometimes, it’s just a tiny setting that’s out of place, but finding it can be a bit like looking for a needle in a haystack, you know?
Are the network settings holding things back for your securely connect remoteIoT?
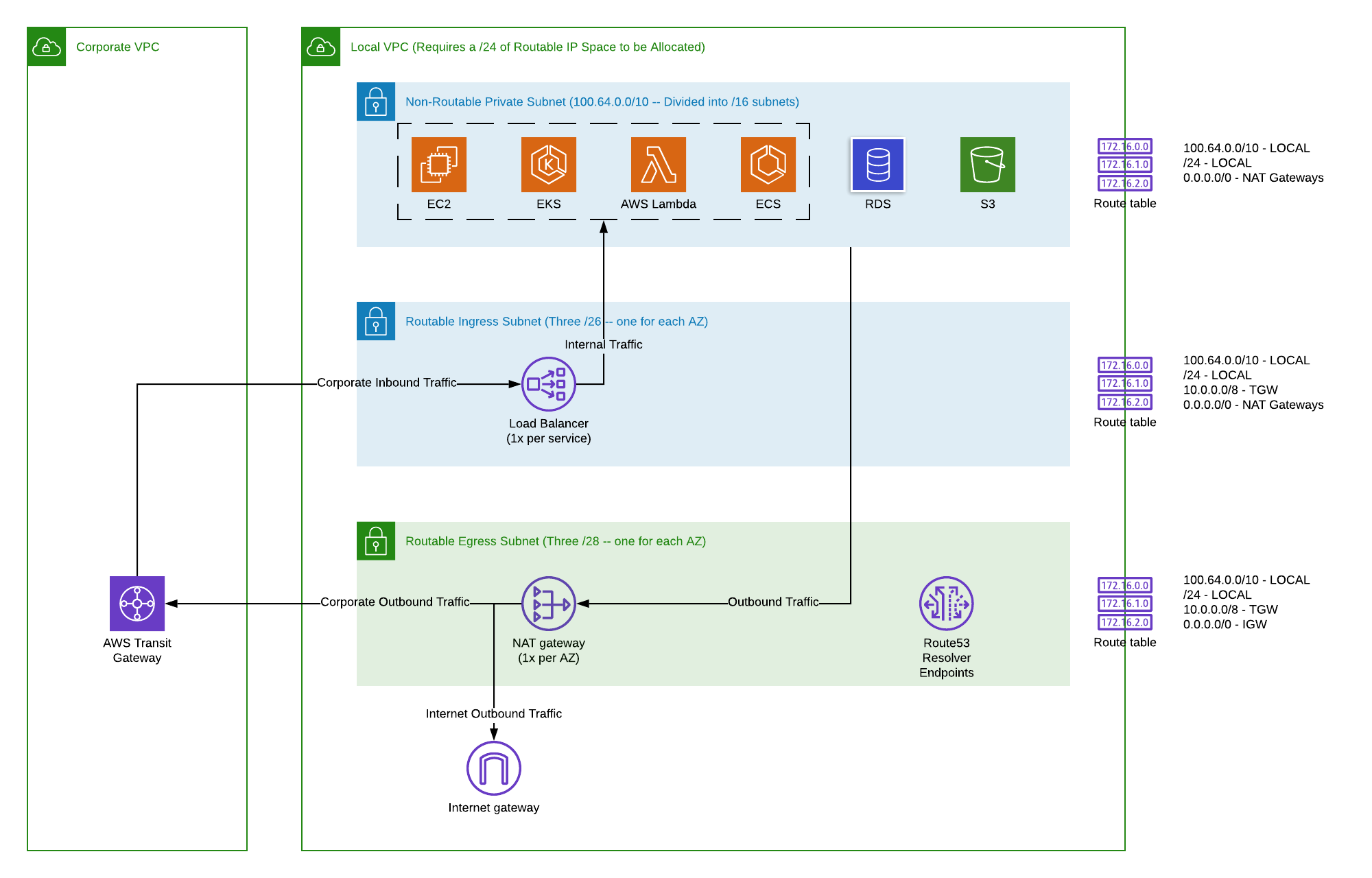
A big part of getting your remote IoT devices to securely connect to your AWS VPC often comes down to the network rules. It's a bit like making sure all the doors and gates are open for the right people, but closed to everyone else. In AWS, these gates are called security groups and Network Access Control Lists, or NACLs. A security group is like a firewall for a specific computer or server inside your VPC, deciding what kind of incoming and outgoing information is allowed. If your IoT device is trying to send data, and the security group on the receiving end in your VPC isn't set to let that kind of information through, then it simply won't get there. It’s a very common spot for things to go wrong.
Then there are NACLs, which are like a bigger, broader set of rules for entire subnets, those smaller sections within your VPC. They control traffic at a wider level, so if a NACL is blocking the specific type of connection your IoT device needs, that’s another potential roadblock. You also have to think about how the information finds its way. Routing tables tell your network where to send information. If the route from your IoT device, through whatever connection method you’re using (like a VPN or Direct Connect), doesn’t correctly point to your VPC, the data will just wander off. It’s really about making sure there’s a clear, approved path for your IoT data to travel. Checking these network settings is usually one of the first things you do when your securely connect remote IoT setup isn't behaving as expected.
- Jaimie Smiles Bio
- Carlos Pr%C3%ADo Odio
- Why Did Winona Ryder And Johnny Depp Break Up
- Lester Holt Health Problems
- Justin Brescia
Sometimes, the problem isn't just about what's allowed in or out, but how the connection is made in the first place. Are you using a virtual private network, a VPN, to extend your VPC network out to your remote devices? Or perhaps you're using something like AWS Direct Connect, which creates a dedicated line between your physical location and AWS. Each of these connection methods has its own set of rules and configurations that need to be just right. For instance, a VPN connection needs its tunnels to be up and running, and the encryption settings have to match on both sides. If there's a mismatch there, your securely connect remote IoT device simply won't be able to establish that initial handshake. It’s like trying to open a lock with the wrong key, in a way. You need to make sure the network path from the device all the way to the specific service or server in your VPC is clear and has the proper permissions at every single hop.
Is your device talking the right language for securely connect remoteIoT communication?
Even if the network pathways are open, your remote IoT device needs to speak the right "language" and have the right credentials to get into your AWS VPC. This means checking a few things on the device itself. First, there are certificates. For secure communication, your IoT device typically needs a digital certificate, which is like a passport that proves its identity. This certificate needs to be valid, not expired, and correctly installed on the device. It also needs to be recognized by AWS IoT Core, the service that helps manage your devices. If the certificate is missing, corrupted, or simply doesn't match what AWS expects, the connection will fail. It’s a pretty basic security step, but it’s easy to overlook.
Next, consider the endpoint. When your device tries to connect, it's trying to reach a specific address, known as an endpoint, within AWS IoT Core. This address is unique to your AWS account and region. If your device is configured with the wrong endpoint, or if there's a typo in the address, it's like trying to send a letter to the wrong house number. The connection simply won't go through. You need to make absolutely sure that the endpoint URL programmed into your remote IoT device is the exact one provided by AWS for your IoT setup. Also, the communication protocol matters. Most IoT devices talk using MQTT, but sometimes HTTPS or other protocols are used. Your device and AWS need to agree on the same way of talking. If your device is trying to use a method that AWS isn't expecting or isn't set up to receive, then that's another reason for a connection problem. It's all about making sure both sides of the conversation are on the same page for your securely connect remote IoT system.
What about identity and access for your remoteIoT in AWS VPC?
Beyond network rules and device settings, a big piece of the puzzle for a securely connect remote IoT setup involves who is allowed to do what. This is where AWS Identity and Access Management, or IAM, comes into play. Think of IAM as the gatekeeper for all the actions that can happen within your AWS account. For your IoT devices, this means having the right IAM policies attached to them. These policies are like rulebooks that say, "This device can send data to this specific topic," or "This device can receive commands from this other service." If your device doesn't have the proper permissions, even if the network path is open and the certificates are good, it won't be able to interact with the services in your AWS VPC. It's a bit like having a ticket to get into a concert, but then finding out your ticket doesn't allow you into the main hall.
You need to make sure that the IAM role or user that your IoT device is using has enough permissions to publish data to AWS IoT Core, and if necessary, to interact with other AWS services within your VPC, like a database or a serverless function. Sometimes, people make the policies too restrictive, accidentally preventing the device from doing what it needs to do. Other times, the policy might be attached to the wrong thing, or it might not be active. It’s also worth checking if there are any VPC endpoint policies that might be restricting access. If your IoT devices are connecting to AWS services through a VPC endpoint, there can be additional policies on that endpoint that further limit what can be done. So, even if your device has a policy, the endpoint might have another policy that overrides or restricts it. It's a layered approach to security, and each layer needs to be correctly set up for your remote IoT connection to work as intended.
Could your firewall be blocking securely connect remoteIoT traffic?
It’s pretty common for firewalls to be the silent blockers when your securely connect remote IoT device isn't talking to your AWS VPC. A firewall, whether it's on the device itself, on the network where the device is located, or within your AWS VPC, acts like a guard checking all incoming and outgoing information. If the firewall isn't told to allow the specific type of communication your IoT device needs, it will simply drop the information packets, and your connection will fail without much of a warning.
On the device side, some IoT devices or the networks they are on might have their own built-in firewalls. These need to be configured to allow outgoing connections to the specific AWS IoT endpoints. If the device's own firewall is too strict, it won't even try to send the data out. Similarly, if your remote IoT device is sitting behind a corporate firewall or a home router's firewall, those network devices might be blocking the necessary ports or protocols. For instance, MQTT often uses port 8883 for secure connections. If that port is closed on any firewall between your device and AWS, your data won't get through.
Within your AWS VPC, beyond the security groups and NACLs we talked about earlier, you might have other firewall appliances or services. These could be AWS Network Firewall, third-party firewalls deployed as EC2 instances, or even just routing rules that send traffic through a specific firewall. Each of these needs to have rules that explicitly allow the incoming connections from your IoT devices, or the outgoing connections if your devices are trying to reach something inside your VPC directly. It’s a bit like having multiple security checkpoints, and if any one of them says "no," then the traffic stops. So, checking all potential firewall points is a really important step when your remote IoT connection to AWS VPC isn't working as expected.
How do you find out what is really happening with your remoteIoT VPC connection?
When your remote IoT device isn't securely connecting to your AWS VPC, finding the exact reason can feel a bit like detective work. The key is to gather clues. Start by looking at the logs. AWS IoT Core provides logs that can tell you a lot about why a device's connection attempt failed. These logs can show you if there's an issue with authentication, like a bad certificate, or if the device is trying to publish to a topic it doesn't have permission for. You can find these logs in AWS CloudWatch. Looking through them can often point you directly to the problem area, whether it’s a policy issue or a device credential problem.
Next, consider network troubleshooting tools. If you suspect it's a network path problem, tools like `ping` or `traceroute` (or `tracert` on Windows) from a machine within your VPC, or even from a test machine near your IoT device, can help you see if the network path is open. You can try to reach the AWS IoT endpoint from these locations. If you can't even get a basic network connection, then you know the problem is likely in the network setup, perhaps a firewall, routing table, or VPN tunnel that isn't quite right. For a securely connect remote IoT setup, you might also use a packet capture tool, like Wireshark, on the device's network to see if the device is even attempting to send data and what kind of response it's getting, if any. This can give you a very detailed look at the network conversation.
Also, don't forget the device itself. Does the device have its own logs? Many IoT devices keep a record of their connection attempts and any errors they encounter. These device-side logs can provide immediate feedback on why it's failing to connect to AWS. It might say something like "certificate expired" or "connection refused." This information, combined with what you see in AWS logs, can paint a pretty clear picture. Basically, the more information you can gather from both ends of the connection – the device and AWS – the quicker you'll be able to pinpoint why your remote IoT isn't securely connecting to your AWS VPC. It's about combining the clues to solve the mystery, so to speak.
What can make your remoteIoT connections to AWS VPC more dependable?
Making your remote IoT connections to AWS VPC more dependable involves thinking ahead and setting things up with care. One key thing is to really get a handle on your IAM policies. Instead of giving broad permissions, give your devices only the specific actions they absolutely need to perform. This is called the principle of least privilege. For instance, if a device only needs to send data to a certain topic, its policy should only allow that. This makes your securely connect remote IoT setup much safer. It's like giving someone only the keys to the rooms they need to enter, not the whole building.
Another good practice is to automate your certificate management. Digital certificates, which are crucial for secure communication, have an expiration date. If you're manually replacing them on hundreds or thousands of devices, it becomes a huge chore and a source of potential outages. Look into ways to automatically renew and deploy these certificates to your devices. AWS IoT Device Management offers features that can help with this, making sure your devices always have valid credentials. This helps keep your securely connect remote IoT connections from suddenly stopping because a certificate ran out of time.
You should also consider setting up monitoring and alerts. Don't wait for things to break completely. Use AWS CloudWatch to keep an eye on your IoT metrics, like connection attempts, successful connections, and rejected connections. Set up alerts so that if something looks unusual – like a sudden drop in successful connections or a spike in rejected ones – you get a notification right away. This lets you react quickly to problems before they become major issues. It's about being proactive rather than reactive, really, so your remote IoT connections to AWS VPC stay up and running more consistently. Also, regularly review your network configurations, including security groups and NACLs, to make sure they still align with your needs and haven't become overly permissive or restrictive over time.
Where do you go when you need more help with your remoteIoT VPC connection?
When you've checked everything you can think of and your remote IoT device still isn't securely connecting to your AWS VPC, it’s time to look for more help. The AWS documentation is a really good place to start. They have detailed guides and troubleshooting steps for AWS IoT Core, VPC networking, and IAM. Often, a specific error message you see in the logs can be searched directly in their documentation, leading you to a solution. It’s a bit like having a very comprehensive instruction manual, you know?
The AWS re:Post community forum is another excellent resource. This is where other users and AWS experts answer questions. If you describe your problem clearly, including what you've tried and any error messages, someone there might have encountered the exact same issue and can offer specific advice. It's a place where you can tap into the collective knowledge of many people who work with AWS every day. You can often find similar questions already answered, too.
For more direct assistance, especially if you have a business-critical setup, AWS Support is available. If you have a support plan, you can open a case and get personalized help from AWS engineers. They can often look at your specific account settings and logs, which can be incredibly helpful for complex problems that are hard to figure out on your own. It's like calling in the experts when you've exhausted your own attempts. So, whether it’s through documentation, community help, or direct support, there are plenty of avenues to explore when your securely connect remote IoT setup is giving you trouble.
This article has covered common reasons why a remote IoT device might struggle to securely connect to an AWS VPC, including issues with network settings like security groups and NACLs, device configurations such as certificates and endpoints, identity and access management policies, and firewall rules. We also explored methods for troubleshooting, like checking logs and using network tools, and discussed best practices for making these connections more dependable, such as applying least privilege and automating certificate management. Finally, we looked at where to find additional help, from AWS documentation and community forums to direct AWS Support.
- Debra Jo Rupp
- Cnn Harry Enten Gay
- Anne Hathaway Net Worth
- Vivienne Jolie Pitt
- Frank Dillane Relationships

Securely Connect Remote IoT VPC AWS Not Working Windows: A

Securely Connect Remote IoT VPC AWS Not Working Windows: A
AWS VPC Subnets, Routing Tables And Internet Access Using, 56% OFF